Radio Free Europe / Radio Liberty
Encrypted messaging apps struggle against authoritarian regimes
From her living room apartment in Tehran, 41-year-old Maryam scrolls through her smartphone in search of posts about Iran that have not been blocked by government censors.
She often turns to Mamlekate, the username of an exiled Iranian in Germany who has created a “channel” on the Telegram messaging app.
Mamlekate uses the Telegram app to repost photos, political commentary, and satire from social media like Twitter and Facebook — which are blocked in Iran.
Maryam says Telegram helps her access information that would otherwise be unavailable to her because of government censors.
“I follow a few channels that post news and satire,” Maryam told RFE/RL. “I don’t really have time to search for information myself, so whenever I have time, I check my Telegram feeds. I also receive funny and interesting stuff from friends on Telegram.”
Encryption Vs. Regime
Telegram is now thought to be the most popular social media application in Iran with some 20 million users.
Worldwide, the popularity of Telegram has soared to more than 100 million monthly users since the start of 2014 — with wide usage in the Middle East, Central and Southeast Asia, and Latin America.
Telegram promotes itself as an encrypted messaging and content-sharing tool for smartphones and computers that allows free international communication with a “secret chat” feature that promises extra protection against eavesdroppers.
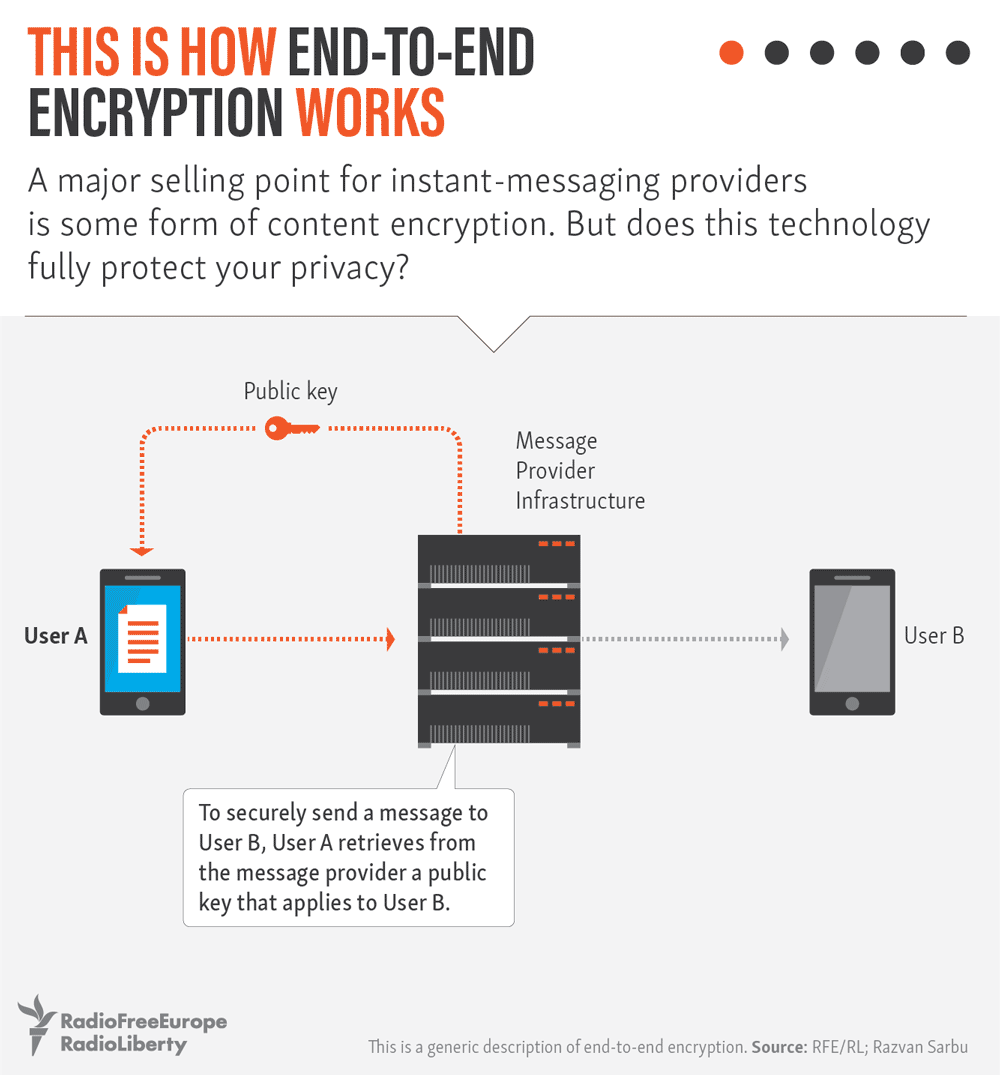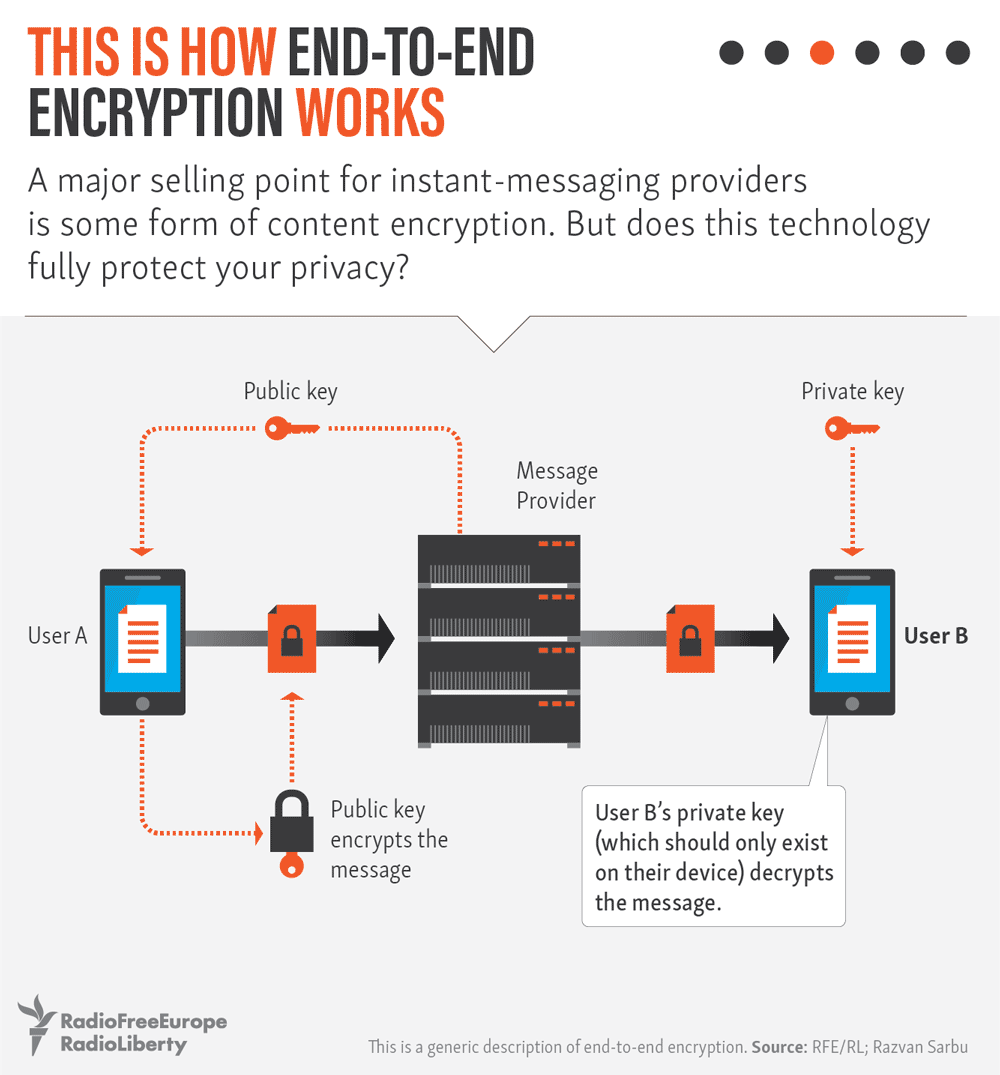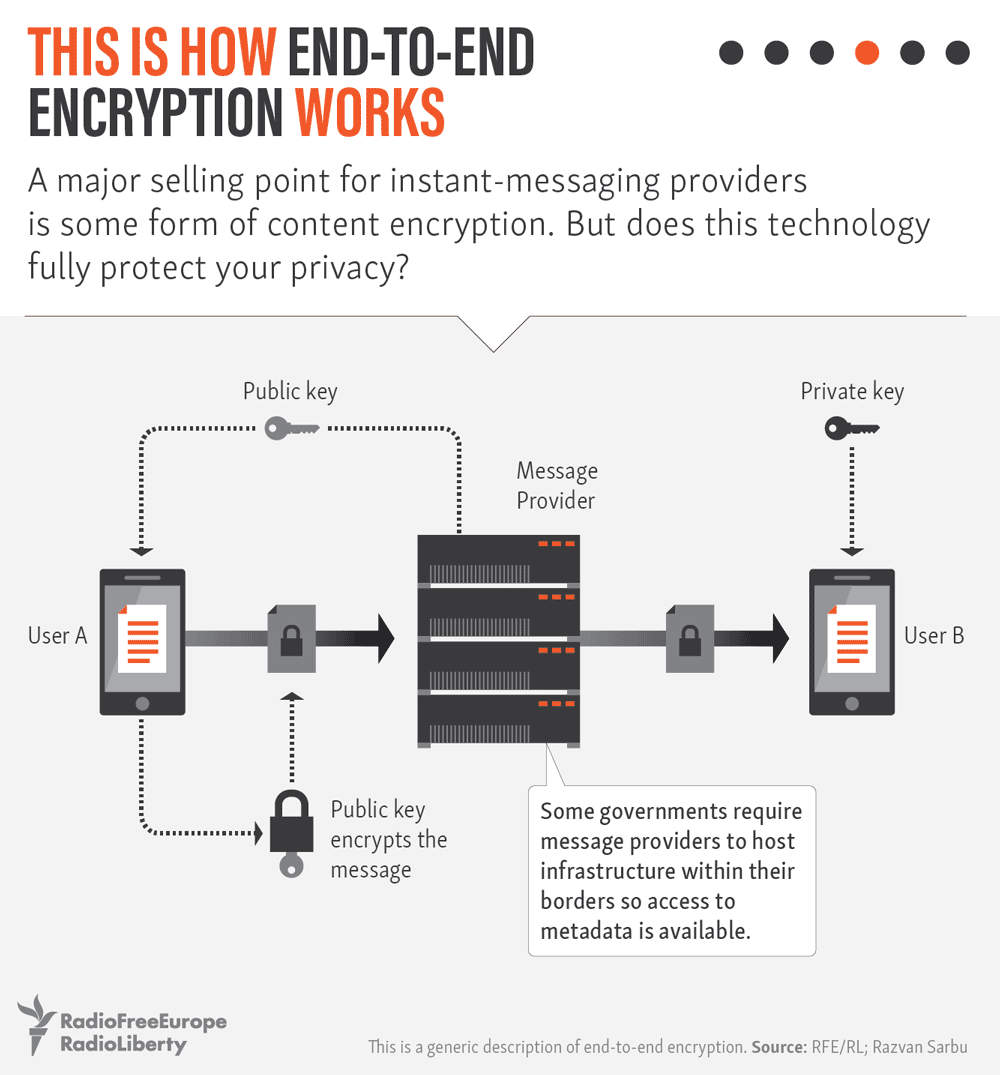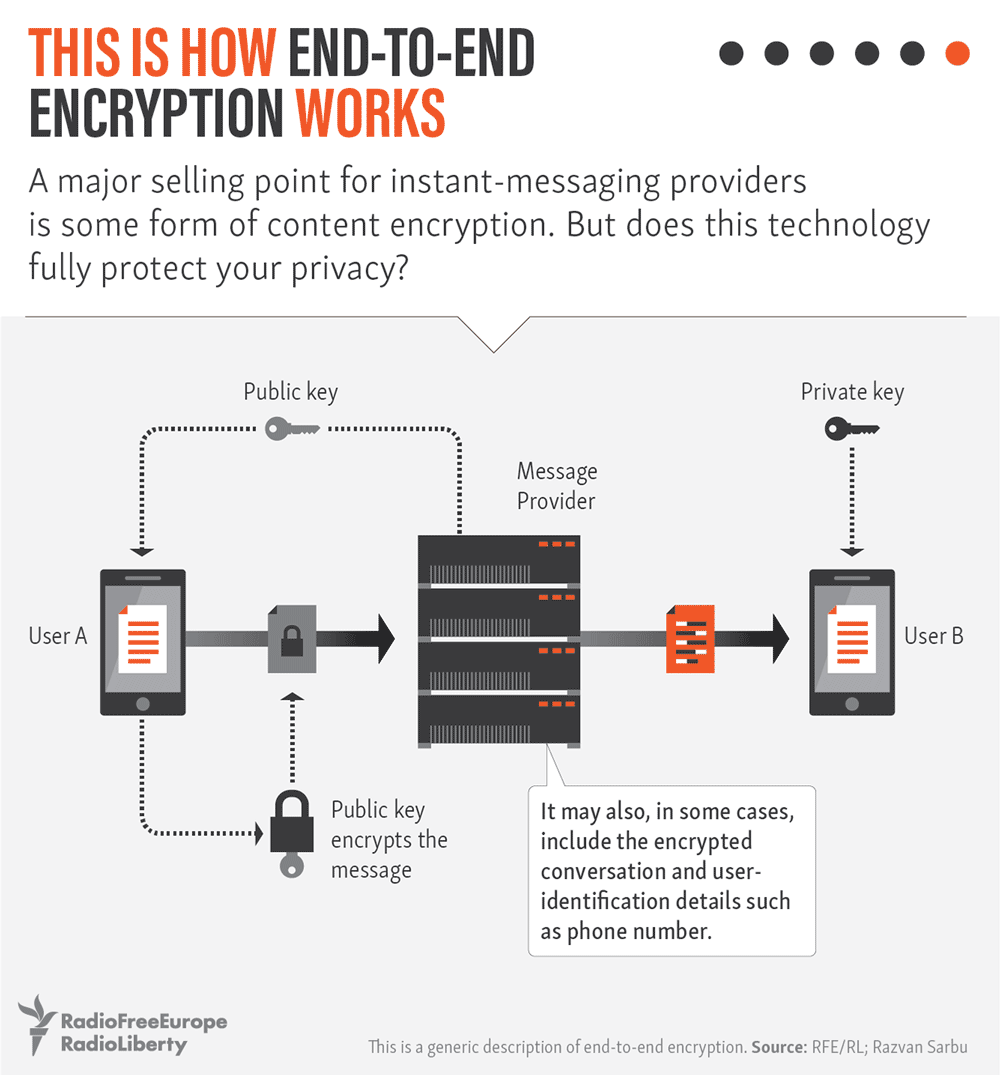
The so-called “secret chat” function allows messages, photos, videos, and scanned documents to be sent using a security protocol known in the industry as end-to-end encryption.
End-to-end encryption is meant to work in a way that doesn’t allow anybody to have the key to see an encoded message except the sender and the recipient — not government monitors, not computer hackers, and not even the messaging service itself. That makes it much harder for third parties to intercept the messages.
But vulnerabilities have emerged. In early August, Reuters reported that an Iranian hacking group known as Rocket Kitten compromised the Telegram accounts of more than a dozen Iranian reformist political activists and opposition organizations.
Washington-based independent cyber researcher Collin Anderson and Amnesty International’s technology expert Claudio Guarnieri said Rocket Kitten also released the identities and Iranian phone numbers of at least 15 million Telegram users.
Other cyber experts said Rocket Kitten’s attacks were similar to ones attributed to Iran’s powerful Revolutionary Guards.
The U.S.-Israeli security firm Check Point says previous attacks by the Iranian hacking group included members of Saudi Arabia’s royal family, Israeli nuclear scientists, NATO officials, and Iranian dissidents.
Anderson and Guarnieri also say Rocket Kitten’s attacks have followed a “common pattern of spearphishing campaigns reflecting the interests and activities of the Iranian security apparatus.
Iran has some of the world’s strictest Internet censorship rules. Thousands of websites are blocked and authorities closely monitor the online activity of political activists and critics of the conservative Islamic government.
Some activists who have been jailed for their online activity have told RFE/RL they were confronted with printouts of their own e-mails when interrogated by intelligence agents and officers from the Islamic Revolutionary Guards Corps (IRGC).
Little wonder, then, that those who discuss sensitive political issues in Iran have been flocking to the promises of a “secret chat” function on the Telegram messaging app.
Subtle Censorship In Tehran
Despite hard-liners claiming the app is a tool for the country’s enemies, the Iranian authorities have allowed the Telegram messaging app to operate in the country — at least for now. Nariman Gharib, a London-based Iranian Internet researcher, says it remains unclear whether Telegram made a deal behind closed doors with Iranian authorities that allows it to continue to operate there.
The financial backer of Telegram is the renegade Russian tech mogul Pavel Durov, who founded Russia’s answer to Facebook — the VK social network — before fleeing his home country under pressure from authorities there.
Durov insisted in 2015 that Telegram “has not entered any agreements with any government on this planet” and does not plan to.
The reality of Telegram operating in countries like Iran is a cat-and-mouse game of subversion and compliance. Iranian officials said in 2015 that they would not tolerate social-networking sites that allow the sharing of “immoral content,” but would allow Internet services if they respect Iran’s “cultural rules and policies.”
In July 2015, Iran’s Deputy Communications Minister Mahmud Khosravi officially complained that the Telegram network “has a problem in Iran.” Soon after that, some Telegram features started to be disabled in Iran — mostly dealing with the sharing of material that Iranian authorities have deemed as obscene.
A few weeks later, Communications Minister Mahmud Vaezi said Telegram had “apologized” to Tehran about offensive message “stickers” — richer, more elaborate versions of emoticons. When those features were disabled, Vaezi said Telegram would be allowed to keep a presence in Iran.
But on October 20, Durov said Telegram was temporarily blocked in Iran for refusing the ministry’s demands to help authorities “read and censor private messages” of Iranian citizens. “We ignored the demand, they blocked us,” Durov wrote on Twitter.
Later on October 20, Durov announced that Telegram was “no longer limited in Iran after a week’s interference and…two hours full blocking.” Durov later retracted his announcement, saying the Telegram app had been cut off in Iran because of a faulty cable connection.
Since then, Telegram has been tolerated by Tehran and the country’s major state-controlled media outlets even operate their own Telegram feeds.
Despite Durov’s insistence that Telegram hasn’t made any deals with Tehran, Internet researcher Gharib says he thinks there is “some kind of cooperation.”
“I just hope it doesn’t create any threats for anyone,” Gharib said. “There are causes for concern over some issues” that raise questions about whether Telegram is cooperating with Iranian censors and surveillance agents.
Anderson and Guarnieri told the Black Hat global information security conference in Las Vegas in August that distinct patterns have emerged regarding the targets of Iranian hackers and Iran’s internal security operations.
In a presentation called Iran’s Soft-War For Internet Dominance, they said hundreds of attempted intrusions by Iranian hackers have focused on high-profile journalists, human rights activists, political figures, Iranian diplomats, adherents of non-Shi’a religions, academics, and nongovernmental organizations that are critical of the Iranian government.
Anderson also has noted that Tehran has a history of trying to control social-media apps that it is unable to completely block by making them “unusable.”
“It’s a more subtle way of getting what you want, which is to coerce people into other services or disrupt access,” Anderson said.
He noted that Iranian President Hassan Rohani’s administration used the same strategy against the Viber messaging and voice-calling app. “Viber wasn’t blocked, but they made Viber so slow that you couldn’t really make long phone calls,” he said. “The intent is a more opaque form of censorship. Just make it so unusable that no one wants to use it.”
Forced Buy-Out
By 2013, Durov realized that there would be a huge international demand for a messaging app with end-to-end encryption after Edward Snowden leaked top secret information about the U.S. National Security Agency’s mass surveillance of electronic communication around the world.
But Durov says he became determined to create Telegram’s encrypted messaging service in December 2011 when Russian security forces arrived at his St. Petersburg apartment and demanded he shut down the VK account of opposition leader Aleksei Navalny. Durov refused and, instead, reported the police action online.
Two years later, in 2013, under pressure from Russian authorities, Durov sold his 12-percent stake in VK. The sale gave a controlling stake to Alisher Usmanov, a billionaire who owns the Russian Internet company Mail.ru and is a close ally of Russian President Vladimir Putin. Mail.ru now owns 100 percent of VK.
In April 2014, after Russia became involved in the war in eastern Ukraine, Russian authorities demanded Durov hand over VK data about Ukraine’s Euromaidan protesters.
Durov refused again and, within days, the Putin loyalists on the VK board fired him as the CEO of VK. Durov promptly left Russia, initially becoming a self-imposed exile in Germany where the headquarters of Telegram were located.
Terrorism And Coup Plots
The main argument governments make for blocking or having access to end-to-end encrypted messaging apps like Telegram and WhatsApp is that they can be used to organize terrorist attacks or acts that threaten national security.
An encrypted chat group in WhatsApp — the global giant acquired by Facebook in 2014 for $19 billion — was used by coup plotters in Turkey’s armed forces on July 15 to coordinate their efforts outside of official military communications channels.
The issue became contentious for Telegram when it was revealed that Telegram was used to coordinate the attacks by Islamic State militants, which killed 130 people in Paris in November 2015.
The debate over personal privacy rights and national security is now at the center of legal and political battles over encryption. It has embroiled all messaging apps and major tech firms — including Google, Facebook, and Apple.
Some governments argue the need for intelligence agencies to have a “backdoor” that gives them access to the encrypted messages of terrorists. But encryption firms and digital-rights groups argue that the very existence of a “backdoor” defeats the purpose of encryption and raises the threat of infiltration by hackers.
New Russian Strategy
Russia’s latest strategy to deal with encrypted messaging apps is contained within a new set of surveillance laws passed by the Duma and signed into law by Putin in July.
The U.S.-based Electronic Frontier Foundation (EFF), an NGO that defends civil liberties in the digital world, describes the Russian legislation as “a set of radical ‘anti-terrorism’ provisions” that include “mandatory data retention and government backdoors for encrypted communications.”
EFF global policy analyst Eva Galperin says the Russian state is imposing “impossible demands” on Internet service providers and other telecommunication companies.
Those firms are required — without a warrant — to give the Federal Security Service (FSB) access to the encrypted communications of messaging services, social networks, e-mails, and any other online services that use encrypted data. While the FSB wouldn’t, in theory, be able to view the content of those messages, the security service would have access to the associated metadata, which could help them establish the identity of a sender.
“They can be ordered to retain every byte of data that they transmit including video, telephone calls, text messages, web traffic, and e-mail for six months,” Galperin says, adding that compliance with the storage-capacity demands of the law could cost Russian Internet service providers trillions of rubles.
Not only would they be required to store all messaging metadata on their servers, they also would have to invest prohibitive amounts of money into new servers to cope with the enormous amount of data.
For Internet service providers, the regulations are due to go into effect in July 2018.
One international encryption firm, Private Internet Access (PIA), already has discontinued its operations in Russia — saying in July 2016 that Russian authorities had seized its servers in the country without notice. PIA encrypts Internet connections and provides anonymous addresses to protect the privacy of users.
Galperin said Russia-based firms that offer messaging services and social-media platforms cannot reasonably comply with all the demands of Russia’s new surveillance laws.
"They become de facto criminals whatever their actions," she said. "And that, in turn, gives the Russian state the leverage to extract from them any other concession it desires. The impossibility of full compliance is not a bug [in the legislation]. It’s an essential feature."
With additional reporting by Golnaz Esfandiari in Prague

